 |
PageBox |
| Support | Map |
|
|
|
|
|
|
|
|
Amazon 1-click analysis
MotivationI help Peter Calveley in his request for the reexamination of the Amazon One-click patent. In 1-click patent family I analyze the family of the One Click patent, and for each application, its examination and the prior art that was considered in said examination.In 1-click prior art I analyze patent prior art identified in the present page. The present page aims to
Note that Peter is still looking for donations to pay the reexamination fee. Click on the Paypal button of this page to donate. I created a mailing list, https://lists.sourceforge.net/lists/listinfo/pagebox-intellectualp. For questions related to this work. For information that could be of interest for parties whose objectives are different from ours send a mail to support@pagebox.net.I added Google search and AdSense advertising to the site in the hope to get money for the reexamination expenses. To support us go to advertiser sites from this page or from the answer pages returned when you use the search button above. 1 clickThe 1-click patent is 5,960,411 filed by Amazon on September 12, 1997. A press release published on October 12, 1999 teaches us that "1-Click combines with Gift-Click and Wish List to make Amazon.com the most convenient, easiest-to-use shopping destination this holiday season. Wish List allows customers to post the gifts they'd most like to receive from family and friends, while Gift-Click allows customers to send gifts easily by entering just the e-mail addresses of their recipients." Amazon patented the Gift-Click function as a continuation of the 1-click application. For details check the 1-click patent family page. The same press release teaches us that Amazon also provided "hassle-free auction bidding with Bid-Click."ClaimsI consider independent claims.Claim 1 reads: A method of placing an order for an item comprising:
Claim 6 reads: A client system for ordering an item comprising:
Claim 9 reads: A server system for generating an order comprising:
Claim 11 reads: A method for ordering an item using a client system, the method comprising:
"A method and system for placing an order to purchase an item via the Internet. The order is placed by a purchaser at a client system and received by a server system. The server system receives purchaser information including identification of the purchaser, payment information, and shipment information from the client system [account setting]. The server system then assigns a client identifier to the client system and associates the assigned client identifier with the received purchaser information [cookie]. The server system sends to the client system the assigned client identifier and an HTML document identifying the item and including an order button. The client system receives and stores the assigned client identifier [cookie] and receives and displays the HTML document. In response to the selection of the order button, the client system sends to the server system a request to purchase the identified item. The server system receives the request and combines the purchaser information associated with the client identifier of the client system to generate an order to purchase the item in accordance with the billing and shipment information whereby the purchaser effects the ordering of the product by selection of the order button." FIG. 2 of the one click patent shows that a unique client identifier and a customer record are created when the user sets an account. A table allows finding the customer record from the client identifier.The description explains that "The client identifier is stored in a file, referred to as a "cookie." A relevant piece of prior art is a publication that describes a system wherein:
Present implementation1-Click Technical Troubleshooting reads:"Your browser must be cookie-enabled in order to use 1-Click shopping. Cookies are short pieces of data stored by your browser which we use to identify your account. If your browser is not cookie-enabled, or if you are using "cookie-trimming" software such as WebFree, Cookie Cutter, Guard Dog, Cookie Monster, or Watchdog, you will not be able to use 1-Click ordering. However, you can still purchase items by adding them to your Shopping Cart and clicking the "Proceed to checkout" button to place your order via our order form." So 1 click works like session and authentication that were standardized (published) before 1 click patent.Using 1-Click at Public Terminals reads: "All transactions made at Amazon.com on our secure server are covered by our security guarantee. However, as an added safety measure, if you are using a public computer terminal or a shared computer, you should turn 1-Click off before you leave the terminal."In other words the cookie is created when you sign in that is deleted when you turn 1-click off. If you do not turn 1-click off the cookie expires after a certain delay and during the while it can be used by someone else to make a purchase. To properly setup a 1-click account you need to provide:
AnalysisIt is not disputed that electronic shopping carts are known art in 1996.
It is also not disputed that the means to not enter twice payment and shipping data was known in 1996:
Users have the opportunity to record their shipping and payment data in a registered user database. To retrieve their data they must enter a unique user ID and password. The user ID is typically the user mail address because (1) the mail address is unique (2) the user remembers her mail address (3) the mail address is useful to confirm the sale, notify the shipping and for marketing purpose. This is a bit like the supermarket card, which can provide (1) special discounts and promotions (2) a fidelity program (3) fast checkout for cardholders. The sequence suggested by the Dr Dobbs reference and other pieces of prior art is the following:
Consider for instance corporate travel applications. The user needs to sign-in first because depending on her position she may be allowed to fly business class or business class with manager approval or economy. 1-click is a kind of one item checkout.
Claim 11 is the weakest. A method for ordering an item using a client system, comprising:
Airline prior art could also break claim 1, a method of placing an order for an item comprising:
It seems reasonable to assume a marketing motivation for one click. In an article entitled "Everything old is new again: obviousness limitations on patenting computer updates of old designs" Richard S. Gruner propose a new obviousness test: "Computer-based updates of prior physical devices or processes are obvious and unpatentable if:
With a vending machine the purchaser first pays and then selects the item. Then the vending machine fulfills the generated order. With a bar tab, there is first an agreement between the customer and the bartender. Then the customer selects the item. The bartender fulfills the generated order and the customer pays at the end of the month. This is close to 1-click and shows that one click is what is provided when it does not make sense to buy more than one item at a time. This is also the case of auctions and of stock markets. The same thing can be said about web shopping carts (that were not patented to our knowledge.) I am not convinced that Web shopping carts were inspired by supermarkets and that the term "Web shopping cart" was not invented a posteriori. Early Web shopping carts such as the one disclosed in the Dr Dobbs article also use the word "catalog" that refers to the catalogs of remote shopping merchants. People received a huge catalog and forms on which they added the items to order. Then they mailed the order form to the merchant that fulfilled the generated orders. Merchants recorded registered users data in a database and these data included shipping data (to send the ordered items and the catalog) and payment data (to send the invoice.)When they moved online - it happened in 80's in France thank to the Minitel - remote shopping merchants computerized the familiar order form and thus implemented the first online shopping carts. They may have implemented an express order feature to order only one item. If they did so they described in their catalog (a written publication) how to use said feature. If they provided said feature with an electronic means like Minitel they probably anticipated 1-click. If they provided said feature with paper they may have made 1-click obvious. Dear readers, if you want to help us please check your catalogs published before September 1997! We believe that the combination of a shopping cart and of 1-click follows from the following findings:
Let us now about written publications describing such means. BN appealAmazon was awarded to Amazon.com on September 29, 1999. On October 21, 1999, Amazon sued Barnes and Nobles (BN) for allegedly infringing on the technology with its "Express Lane" feature. In December 1999 a district court granted a preliminary injunction to Amazon [BN could not use Express Lane for the Chrismas sells.] An appeal court overturned this preliminary injunction in February 2001. In March 2002 Amazon and BN settle the 1-click lawsuit. In September 2002 the Free Software Foundation decided to end its boycott of Amazon.I present here the appeal court decision. The appeal court was not deciding about the alleged infringement or the validity of the 1-click patent. The appeal court was deciding whether Amazon had presented a case showing such a likelihood of infringement by BN that a preliminary injunction could be awarded. Amazon was entitled to a preliminary injunction if it could succeed in showing:
"We hasten to add, however, that this conclusion only undermines the prerequisite for entry of a preliminary injunction. Our decision today on the validity issue in no way resolves the ultimate question of invalidity." The appeal court came to the conclusion that 1-click is a matter of step order:"Col. 3, ll. 31-37. How, one may ask, is the number of purchaser interactions reduced? The answer is that the number of purchaser interactions is reduced because the purchaser has previously visited the seller's web site and has previously entered into the database of the seller all of the required billing and shipping information that is needed to effect a sales transaction. Thereafter, when the purchaser visits the seller's web site and wishes to purchase a product from that site, the patent specifies that only a single action is necessary to place the order for the item. In the words of the written description, "once the description of an item is displayed, the purchaser need only take a single action to place the order to purchase that item." Col. 3, ll. 64-66." The appeal court found that 5,708,780 from OpenMarket was relevant prior art. The court wrote: "States Patent No. 5,708,780 ("the '780 patent") (a reference cited by BN which is discussed more fully below), describes "forwarding a service request from the client to the server and appending a session identification (SID) to the request and to subsequent service requests from the client to the server within a session of requests.""Before the district court, BN argued that this reference anticipated at least claim 1 of the '411 patent. In the preferred embodiment described in the '780 patent, a user browses the web conventionally, and a content server provides web documents to the user and determines when the user seeks access to "controlled" content, i.e., web pages for which the user needs authorization to browse. '780 patent, col. 7, ll. 35-38. The '780 patent describes a system in which controlled pages are returned to the user's browser when an authorized request is received by the content server. We note that the '780 patent describes "forwarding a service request from the client to the server and appending a session identification (SID) to the request and to subsequent service requests from the client to the server within a session of requests." Id. at col. 3, ll. 12-16. "We conclude that the district court failed to recognize that a reasonable jury could find that such "items" (i.e., controlled pages) fall within the scope of the claimed invention, and that delivery of these controlled pages based on receiving an authorized request from a user's browser may constitute a "single action ordering component" within the meaning of the claims in the '411 patent. Therefore, the '780 patent is yet another prior art reference cited by BN which tends to raise a substantial question of validity, either alone or in combination with the other cited references."StatsI identify here the most frequent words.
A search on USPTO with "spec/order and spec/client and spec/item and spec/modem and (spec/purchaser or spec/customer or spec/buyer)" returns 1343 patents including:
Special phone numbers in which the TELCO collects the fee on behalf of the provider are probably too far from 1-click. A search on USPTO with "spec/buy and spec/client and spec/item and spec/modem and (spec/purchaser or spec/customer)" returns 334 patents including:
BountyQuest findingsIn a paper entitled "BountyQuest Revisited: The Coin Has Two Sides" published on april 2, 2001 Nancy Lambert reports that:"in an open letter again available from the BountyQuest site (full text at http://www.oreillynet.com/pub/a/patents/2001/03/14/bounty.html) dated March 14, O'Reilly said "[B]ecause of the complexity of Amazon's complete patent, and because it is specific to the Web rather than to these earlier media, we weren't able to match every claim. And, in fact, all the prior art that was submitted specifically for the Web [my emphasis-NL] confirms Amazon's belief that they were doing something original.... So, I want to offer Jeff something of an apology. Amazon may not have deserved a patent on 1-Click... but they appear to have been staking out new territory in ease of use for Web shopping." Then he flipped the coin again, saying, "However, we do think that the prior art that we found sufficiently narrows the scope of what Amazon can claim [so] that it will be much more difficult for them to enforce their patent."Some Bountyquest findings were disclosed: ""O'Reilly agreed that he would award the $10,000 to those who submitted the nearest prior art. BountyQuest later announced that it would split the bounty among three Hunters. The winning art includes US4734858, which describes the use of a remote data terminal to place orders; US5303393, which describes a simplified way of placing an order via a two-way radio system; and European patent EP680185 (U.S. equivalent US5819034), which actually describes one-click shopping within the patent specification."The abstract of 4,734,858 reads: "A plurality of data terminals which can automatically dial a local processing center (LPC) are distributed among users each of whom can address the LPC with a unique user identification and an internal terminal identification."[Terminal identification was almost ubiquitous (see SNA LU2 for 3270 for instance). In SNA there were 370 computers running MVS/CICS, 3705/3725 network controllers running NCP to which were connected 3274/3174 cluster controllers to which were connected 3270 devices. SNA could use phone lines - for instance a remote 3274 connected to a central 3705. X25 was supported through an NCP subprogram called NPSI.] "Each data terminal can accumulate orders for goods or services in a send memory while the terminal is unencumbered by any external connector." [items orders are accumulated in a kind of shopping basket.]5,303,393 is relevant: "The user has the option of inputting to the mobile terminal 401 a user-input signal. The user can generate the user-input signal by speaking into a microphone which converts the user's voice to a digital signal processes the converted voice signal to generate a user-input signal. For example, the user might speak the word ORDER which indicates to place an order of the item being advertised in the advertisement of the program signal. The spoken word ORDER is converted to a digital signal, identified and recognized. The resulting output is the user-input signal. Alternatively, the user may place an order by pushing a button or touching a touch screen on a display."EP680185 / 5,819,034 reads: "When a viewer wishes to order an item, a button is pressed on the TV remote control. This button signals the client computer 22 to display a series of instructions and menus necessary to solicit the information necessary to place the order, e.g. the item number, name and address of the viewer, the method of payment, the credit card number (if needed),"This is in the context of interactive TV. "If needed" means that this piece of information can be entered once: "It is also possible that permanent information about the viewer (i.e. the name, address, method of payment and credit card number) may be preentered once by the viewer, so it is not necessary to solicit that information each time an order is placed. The information is stored in permanent memory in the client computer. In such a case, when an order is placed, that information is retrieved from the permanent memory, appended to the item number and transmitted to the central computer."ApproachWe identify environments in which 1-click may have been practiced first. Such environments must include:
XanaduThe specification of 1-click describes a Web invention. My gut feeling is however that there is no prior art to find in Xanadu, the Web ancestor. The big problem is that Xanadu was never released. So there are few artcles and no third parties' tutorials. Nevertheless the following URLs are of interest:
DimensionsThere are three dimensions to consider in prior art:
HTTP/HTMLThe RFC 2109 (February 1997) describes the HTTP state management. RFC 2109 reads:'The origin server initiates a session, if it so desires. (Note that "session" here does not refer to a persistent network connection but to a logical session created from HTTP requests and responses. The presence or absence of a persistent connection should have no effect on the use of cookie-derived sessions). To initiate a session, the origin server returns an extra response header to the client, Set-Cookie.' There are two other solutions addressing the session / state management issue:
GET http://www.amazon.com/gp/amabot/?pf_rd_uri=/gp/yourstore/ref=pd_irl_gw/002-0045386-6367261?%5Fencoding=UTF8&signIn=1&pf_rd_p=103946401&pf_rd_s=ilm&pf_rd_t=101&pf_rd_i=507846&pf_rd_m=...&pf_rd_r=... HTTP/1.0 It looks like Amazon implements something similar to 5,966,705, a patent filed on June 30, 1997 by Microsoft whose title is "Tracking a user across both secure and non-secure areas on the Internet, wherein the users is initially tracked using a globally unique identifier." The detailed description of 1-click teaches that cookies are used:The client identifier/customer table 212 contains a mapping from each client identifier, which is a globally unique identifier that uniquely identifies a client system, to the customer last associated with that client system. The client system 220 contains a browser and its assigned client identifier. The client identifier is stored in a file, referred to as a "cookie." In one embodiment, the server system assigns and sends the client identifier to the client system once when the client system first interacts with the server system. From then on, the client system includes its client identifier with all messages sent to the server system so that the server system can identify the source of the message. As exposed in RFC 2109 a cookie stores name value pairs. From the current implement and description we can deduce that the cookie is created when the server processes a request on http://www.amazon.com and that a new name value pair clientid = xxxxx is added to the cookie when the user signs in or that a new cookie with possibly a longer expiration time is created. The creation of a session logically implies the creation of a session block on the application server and each time the client browser sends a request with the same cookie / url the server logic retrieves the session block. The session block contains objects such as the client data. Writing a client identifier name value pair can serve three purposes:
Regarding the way the client ID is generated, the abstract of 1-click reads: "The server system receives purchaser information including identification of the purchaser, payment information, and shipment information from the client system. The server system then assigns a client identifier to the client system and associates the assigned client identifier with the received purchaser information."A reasonable implementation is:
"request including the identifier so that the server system can locate additional information needed to complete the order and so that the server system can fulfill the generated order to complete purchase of the item." The identifier contains what is needed to locate customer information. The issue is closely related to infringement. I think that an id that uniquely identifies a temporary session block that contains or points customer information infringes 1-click as well as an id that permanently identifies a customer record. Claim 9 reads:"an order placement component that retrieves from the data storage medium information for the indicated user." The disclosure does not define "data storage medium." The Free Dictionary and Wikipedia suggest that a data storage medium is something like magnetic/optical storage or flash memory. Another limitation of claim 9 reads:a data storage medium storing information for a plurality of users. Another limitation of claim 9 reads:a request including an indication of one of the plurality of users So an indication is provided that is sufficient in the current state of the server to retrieve user information from the data storage medium, which is consistent with claims 1 and 6.My understanding is that certificate-based identification also qualifies. Certificates, signatures and public key infrastructures work in the following way. The requestor presents some credentials like her cardholder name, credit card number and expiration date to a certificate authority. The certificate authority returns:
Public key infrastructure provide non-repudiation. Given that
In a typical implementation of 1-click with certificates the server would act as a certificate authority. The abstract of 1-click: "The server system receives purchaser information including identification of the purchaser, payment information, and shipment information from the client system. The server system then assigns a client identifier to the client system and associates the assigned client identifier with the received purchaser information."would translate into: The server system receives purchaser information including identification of the purchaser, payment information, and shipment information from the client system. The server system then creates a key pair and a certificate. It sends the private key and the certificate to the client and associates the certificate with the received purchaser information. Then the client can be asked to sign a message and hence to use her private key.Certificates are likely to be used in prior art and particularly in patents for the following reasons:
"A computerized, electronic purchase mediating system includes a purchaser database having a list of purchasers and a merchant database having a list of merchants. The purchaser database stores information about each purchaser including a set of personal payment methods that the purchaser could use to purchase goods and/or services. Similarly, the merchant database stores information about each merchant including a set of accepted payment methods that the merchant would accept for sale of the goods and/or services. The purchase system also includes a processor coupled to the purchaser and merchant databases. The processor receives a purchase request and accesses the merchant database according to a merchant identified in the purchase request to retrieve the set of accepted payment methods which corresponds to that merchant. The processor also accesses the purchaser database to retrieve the set of personal payment methods which corresponds to the identified purchaser. The processor then computes an intersection of these two sets to derive a common set of any available payment method that is both accepted by the merchant and can be used by the purchaser for purchase of the goods and/or services. The purchaser is presented with the purchase amount and the common set of available payment methods to choose a most preferred form of payment. Upon selection, the processor consummates the sale and signs a digital signature with the purchaser's permission via password verification to ensure for the merchant that a completed transaction has occurred." We can compare the limitations of the first claim of 1-click to 5,878,141:under control of a client system is practiced by 5,878,141. "Purchasing system 10 also has multiple purchasing terminals 18-23 located remotely from transaction processing unit 12. Purchasing terminals 18-23 are illustrated as many different types of electronic devices, including a point-of-purchase register 18, a personal computer 19, a telephone 20, a stand-alone machine 21 (e.g., an ATM), a television and set-top box unit 22, and a magnetic-stripe credit card reader 23 (e.g., a Verifone.RTM. reader). Each purchasing terminal has an input device which can receive a purchase request from a purchaser to buy goods and/or services from a merchant. The input device can be in the form of a keypad (as in the case of the register 18, telephone 20, stand-alone machine 21, and card reader 23) or a keyboard or mouse (as in the case of computer 19), or a remote control device (as in the case of a remote for the TV and set-top box unit 22). These illustrated purchase terminals are only a representative sample, as many other electronic devices can be used to make purchases in the computerized purchasing system of this invention."displaying information identifying the item is practiced by 5,878,141. 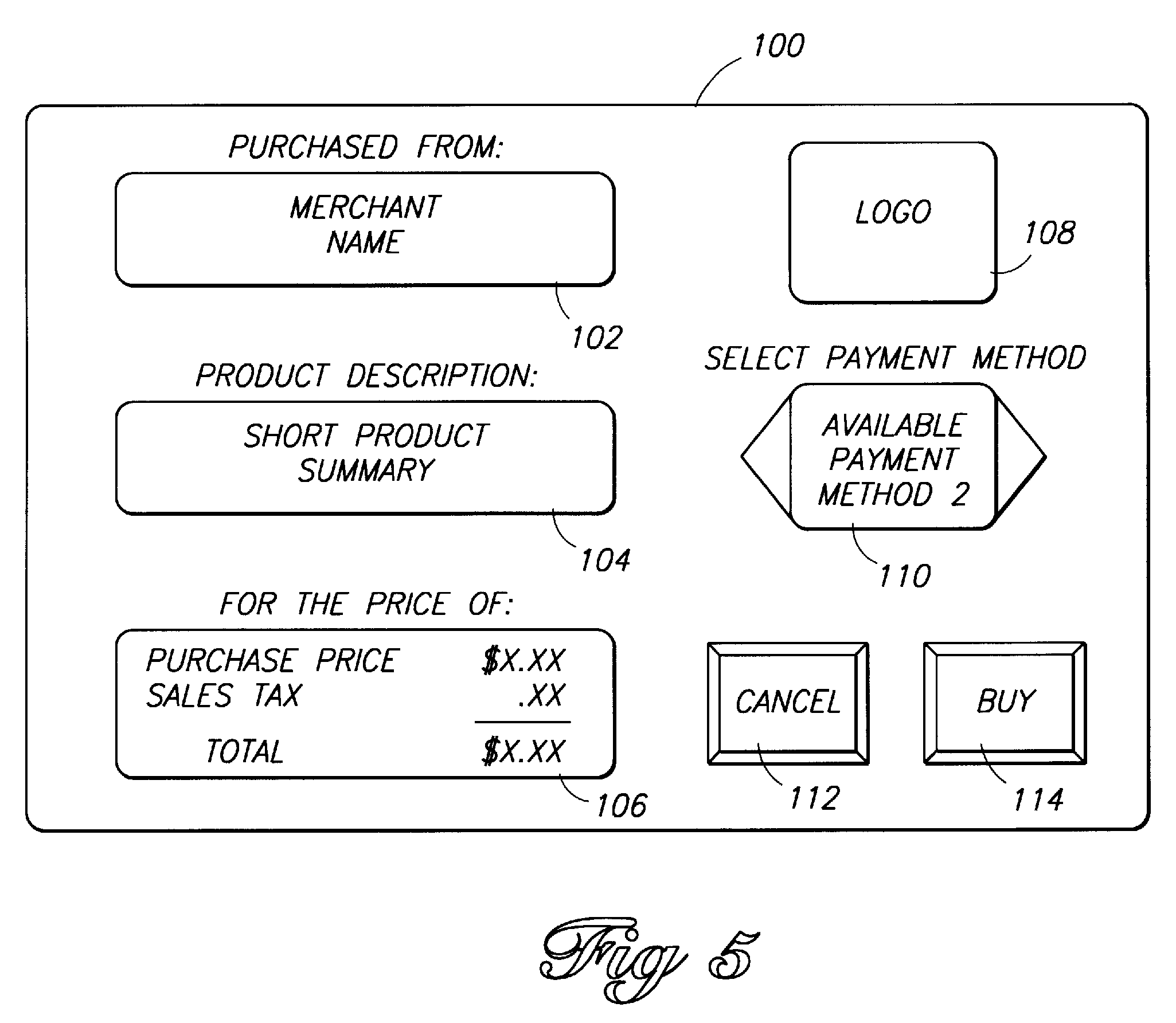
FIG. 5 is a user interface that is displayed on a television of the interactive television system during a purchase transaction. in response to only a single action being performed is practiced by 5,878,141.See Buy button on FIG. 5. "A cancel button 112 and a buy button 114 enable the subscriber to accept or deny the transaction before any money exchanges hands."Regarding the selection of the payment method: "FIG. 5 is but one example arrangement of information that can be presented to the subscriber, and many other arrangements with more or less information can be used."So there can be less information and "[the user interface] includes a spin dial 110 which presents the available payment methods in a sequential order, and if desired, in a prearranged order according to the subscriber's preferences."So Microsoft teaches that the preferred payment method can be displayed first. This is the default: "The subscriber selects the default payment method, or cycles through any alternative choices, to inform the purchasing system of a desired payment method."Note that 1 click teaches a method describing client / server interactions and is silent on what happens in the client system, and
"If the purchaser confirms the purchase transaction, the processing unit attaches an unforgeable digital signature on behalf of the purchaser to authorize the purchase and to validate for the merchant that a sale has been consummated. The digital signatures are produced using signing tools, such as cryptographic signing keys, which are unique to corresponding purchasers and are stored in the purchaser database. A password entered by the purchaser authorizes the processing unit to use his/her associated signing tool kept in the purchaser database. This digital signature assures the merchant that a legally enforceable purchase transaction has occurred." The digital signature is unique to corresponding purchaser. It is an identifier of a purchaser.receiving the request; "The transaction routing system selects a subscriber account." generating an order to purchase the requested item for the purchaser identified by the identifier in the received
request using the retrieved additional information; and The background of 1 click reads: "When the user has completed selecting the items to be purchased, the server computer system then prompts the user for information to complete the ordering of the items. This purchaser-specific order information may include the purchaser's name, the purchaser's credit card number, and a shipping address for the order. The server computer system then typically confirms the order by sending a confirming Web page to the client computer system and schedules shipment of the items."1 click does not even include the words withdraw and deposit though we can reasonably assume that there is a withdrawal and a deposit at the same time as the shipment - a word that is not used in the Microsoft patent even if it has to happen when the item is a good and not a service. Here there is inherency on both sides.For the patents cited by 5,878,141 or that reference 5,878,141 check the 1-click priorart page. GUIThe name of the topics are chosen for keyword search and not for technical accuracy. Hypercard, Visual basic, Delphi and Powerbuilder are IDEs that produce programs that implement GUIs, possibly with the help of runtime libraries. Java is a language. A browser is the graphical program that interprets HTML pages.Programs widely used in 1996 that could have used implement the client part of a client server application were:
It has to be said that numerous BBS provided GUIs to their customers and that these GUIs may have implemented 1-click. The appeal opinion mentions CompuServe Trend which was a tool belonging to this family. Beside commercial products there was already free open source products. The most popular was tcl/tk. The graphical part of tcl/tk, tk could be used with other languages. There was for instance a perl/tk. And programmers wrote GUI with traditional languages, Pascal and C, later C++ and a graphical API.HyperCardHyperCard was a program developped for the Apple MacIntosh by Bill Atkinson. Hypercard was released in 1987. A HyperCard program was a stack. It contained a graphical background and cards containing text, graphics, fields and buttons linking to other cards or running scripts. The script language of HyperCard was HyperTalk. It was able to call external programs. As early as 1987 was suggested that HyperCard could become the center of the MacIntosh. In 1992 there was a HyperCard TCP toolkit allowing implementing TCP/IP communications from within HyperCard. HyperCard stacks have probably also been developped to use the AppleLink. However this service was expensive and targeted Apple employees, dealers and developers. This is unclear whether an online ordering card was implemented and described in a written publication such as MacTutor.Note that because AppleLink (and the Microsoft equivalent, MSPN) were used by developers an application can have implemented and publicly described, for instance to get patches, add-ons and alpha/preview releases:
HyperTalk programming was somewhat similar to Javascript or Visual Basic programming. In 1996 a company called Royal Software released a LiveCard product to serve HyperCard stacks on the Web. It was not enough to stop the decline of HyperCard and Apple eventually stopped distributing it despite user campains. Several alternatives to HyperCard were developed. Quite interestingly the first version of HyperCard was free - but the distribution cost which was high with the Apple packaging. This was the wish of Bill Atkinson. About the failure of HyperCard it is useful to reproduce here an answer of John Sculley, then Apple CEO. The question was "Any missed opportunities that you wish you could do over?" He replied:As I look back on things that I wished we would have done differently when I was at Apple, I think one of the biggest missed opportunities, and it was on my watch, so I feel responsible and disappointed that we didn't do more with it, was Hypercard. It was created back in 1987 by Bill Atkinson, Apple's first software programmer. We could never figure out exactly what it was. We thought it was a prototyping tool. We thought it was a database tool. It was actually used by people as a front-end communications device for TCP/IP to connect the Internet to large Cray computers. We weren't insightful enough to recognize that what we had inside of Hypercard, essentially, was everything that later was developed so successfully by Tim Berners-Lee with HTTP (Hypertext Transfer Protocol) and HTML (Hypertext Markup Language). We didn't call it that. But essentially, we had all that hypertext, radio buttons and linking capability architected in the original Hypercard. In hindsight, I wish Apple had recognized that we had a huge opportunity to go take our user interface culture, and our know-how, and applied it to the Internet. I think we would have had a very different story for Apple during the 1990s. But that, of course, is hindsight. There is a Hypercard FAQ you can find here and here. For a more comprehensive HyperCard story you may look here.Visual BasicI started using VB with version 4. Then I moved to 5 and 6. So I know only the 32-bit version. VB was quite effective to quickly develop a user interface and could be extended with controls called VBX in the 16-bit version and OCXs in the 32-bit version. Technically a VBX was a DLL whereas an OCX was a OLE 2 control (later known as an Active X control.) Controls were typically written in Visual C++ with the MFCs and later the ATLs in case of OCXs.) Therefore it was possible to call any kind of server from VB.Here I probably need to talk about the client / server protocols build on top of TCP/IP and UDP. There were:
DelphiDelphi was a development package developped by Borland. Delphi 1 released in 1995 was 16-bits. Delphi 2 released in 1996 was 32-bits. Delphi comprised
PowerbuilderPowerBuilder was development package developped by Powersoft. It was more expensive than VB and Delphi et particularly effective for direct database access. I include PowerBuilder because it was as good as VB and Delphi to write the client part of a client server application. A search on the USPTO site with "spec/powerbuilder and spec/buy and spec/item and spec/list" returns 44 patents.NetworkFirst generations of PDA (Newton) were using Radio Frequency networks.A comparatively small number of people was using networks up to the time in 1995 at which AOL introduced its cheap rate and massive advertising campaigns with the exception of France in which a simple device embedding a modem, the Minitel, was given away to phone subscribers. There were three barriers before:
TCP/IPHere I do not aim to present TCP/IP, Internet and the Web. I assume that this network, infrastructure and environment are familiar to the reader. There are a number of excellent documents on the subject such as the Wikipedia articles about the Internet protocol suite, Internet and the World Wide Web. You can also read Internet Structure and Development: On Strategic Uses of the Archetypes of the Networked Mind.I aim to present in which way TCP/IP, Internet and the Web may have been used in systems and methods antipating 1-click. Originally TCP/IP was frequently confused with Unix (the first operating system implementing the TCP/IP stack) and Ethernet (the first data link layer used by TCP/IP in LANs.) Outside the Unix world the confusion probably lasted up to 1994. In the 80's planners (notably in Europe) considered TCP/IP as an interim solution before OSI (discussed in the X25 section.) On the LAN Ethernet was challenged by the token ring of IBM and the TCP stack was challenged by numerous systems, the most popular being Novell with the IPX and SPX protocols. TCP/IP was primarilly designed for LAN and it looked weird at first to send TCP traffic on a serial line (with SLIP first and then with PPP.) OSI failed notably because
TCP identification data comprise:
The TCP protocol is described by RFC 793. TCP is layered on top of IP: +---------------------+ | higher-level | +---------------------+ | TCP | +---------------------+ | internet protocol | +---------------------+ |communication network| +---------------------+So an IP datagram contains a TCP segment. An IP datagram has a header that contains the source and destination addresses: 0 1 2 3 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ |Version| IHL |Type of Service| Total Length | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Identification |Flags| Fragment Offset | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Time to Live | Protocol | Header Checksum | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Source Address | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Destination Address | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Options | Padding | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+A TCP segment has a header that contains the source and destination ports: 0 1 2 3 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Source Port | Destination Port | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Sequence Number | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Acknowledgment Number | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Data | |U|A|P|R|S|F| | | Offset| Reserved |R|C|S|S|Y|I| Window | | | |G|K|H|T|N|N| | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Checksum | Urgent Pointer | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Options | Padding | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | data | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+Therefore every time data are sent the source and destination addresses and ports are sent. There is another transport protocol, UDP that was probably not used by prior art. This protocol is defined by RFC 768. A search on the USPTO site with "spec/"tcp/ip" and spec/buy and spec/item and spec/list" returns 319 patents. However probably not more than thirty applications using TCP/IP were filed before the web advent. I found the following patents:
X25I mean here the layer 3 of the OSI model (there is another article on Wikipedia describing the OSI protocols.) X25 programming was similar to UDP programming and as such somewhat easier than VTAM (see below) programming.See the Wikipedia article for the story of X25. A client / server application can have been implemented with X25
For a presentation of the X25 protocol you can look at X25 and Troubleshooting X.25 Connections from CISCO. The AIXlink/X.25 Version 2.1 for AIX: Guide and Reference is an example of X25 API. A search on the USPTO site with "spec/x25 and spec/buy and spec/item and spec/list" returns three patents including
IBMIn early 90's IBM had two families of server computers:
A method for carrying out computerized trading of goods, comprising the steps of:
IBM was not the only mainframe provider. Beside compatible makers (Amdahl and Hitachi) there was the BUNCH, comprising Burroughs that introduced the stack and the compiled kernel, Unisys that made the first commercial computer and was as successful as IBM in online reservation, NCR (stands for National Cash Register - Watson who created IBM came from NCR,) Control Data, the pioneer of supercomputers and Honeywell that bought the General Electric's computer division that created MULTICS, the operating system that inspired Unix. The computer industry is a winner-take-all industry. In early 70's IBM emerged as the clear winner but (1) people were not aware of the winner-take-all thing (2) IBM was refrained to kill its competitors by antitrust law. So the bunch produced mainframes a while (Burroughs and Univac merged to form Unisys, Honeywell sold its computer division to Bull) and also made interesting things. CRSs provided since 60's a near-Web function to the travel agent community. These systems were frequently using IBM mainframes with another operating system, TPF. CRSs were providing the hardware and setting the network for the travel agents which were their customers. CRSs were also providing a book describing cryptic commands. For instance to book a flight the travel agent
For prior art searches we cannot use IBM, notably because IBM is the biggest patent owner and because IBM produced almost every kind of hardware. Different keywords can be considered, SNA, SDLC (the serial line protocol), BSC that was used before VTAM. Transaction monitors like CICS and IMS can be used. Nevertheless the best keyword is probably 3270 that refers to both the terminal and the presentation layer. A search on the USPTO site with "spec/3270 and spec/buy and spec/item and spec/list" returns 51 patents including:
DigitalWhen IBM was the mainframe leader Digital Equipment (DEC) was the minicomputer leader. Digital was targeting education, labs and manufacturing when IBM was targeting small business with its AS/400 systems. The main competitors of Digital were Data General and HP. Then Compaq bought Digital and HP bought Compaq. Four families of Digital computer were famous:
Big BBS servers were usually VAXes running VMS. Digital created the CRT terminals whose emulations are still used today: To search prior art related to Digital the best keywords are probably VAX and VMS. A search on the USPTO site with "spec/VAX and spec/buy and spec/item and spec/list" returns 17 patents including:
Terminals"Dumb" terminals were the aforementioned VT terminals from Digital and teletypes. It is important to make the difference between teletypes, teletype emulations (and the devices provided by CRSs and airlines though they were manufactured by IBM and UNIVAC) and not-so-dumb VT terminals.Teletype-like devices allowed displaying this: Items offered for sale: 1 item 1 $20 2 item 2 $99.5 3 item 3 $44 Enter your choice:What the user entered was displayed after the data previous sent by the server (here after "choice:".) The user entered text and pressed the enter key to notify the server that her input could be processed. The VT100 was more capable. vi is a good illustration of what vt100 allowed. You move the cursor down one line when you press the j key. You move the cursor up one line when you press k. You move to a command mode - the cursor being at the bottom of the line when you press the : key. On Unix you can develop a similar full screen text user interface with a library called curses. Such text user interface was terminal-independent (VT100 and more capable terminals such as the VT220.) The mapping of the terminal control sequences is described in a termcap/terminfo file. Here is an example of terminfo database.curses was not easy to program. Few end-user developments were made with curses. It took weeks to write a curses interface (usually in C) when it took hours to write a teletype interface (typically using shell.) However products from vendors such as Oracle allowed creating curses forms. I would like now to show how this terminal discussion translates in possible anticipation of 1-click.A shopping server allows users to register. This registration may use mail, e-mail, phone call or any other means. The customer provides her payment data - not necessarilly card data, bank account data can be used - and shipping data. Once the request is approved the administrator
1 echo "Items offered for sale:"
2 echo "use db; select id, name, price from items;" | mysql -u$DBUSER -p$DBPASSWORD
3 echo "Enter your choice:"
4 read choice
5 echo "use db; select payment_data from customers where name='$LOGNAME';" | \
mysql -u$DBUSER -p$DBPASSWORD >payment_data
6 echo "use db; select shipping_data from customers where name='$LOGNAME';" | \
mysql -u$DBUSER -p$DBPASSWORD >shipping_data
7 echo 'use db; insert into order ("customer", "id", "time", "payment_data", \
"shipping_data") values($LOGNAME, $choice, `date`,
`cat payment_data`, `cat shipping_dat`)' | mysql -u$DBUSER -p$DBPASSWORD
The script get the item list from a table items of the db database. Then it reads the user input in a choice variable,
retrieves the shipping and payment data from the customer table and adds a record to an order database containing the
customer name, the item id, the time at which the customer ordered the item, the payment and shipping data.
A second script reads the order table and fulfill the order. In this example I use mysql but it works as well with another relational database or even with Berkeley DB.Now we can check whether this implementation infringes (or anticipates if it was published before September 1997) the first claim of the 1-click patent.
A written publication (for instance a user guide) will not necessarily teach all limitations. The most generic search term is VT100. A search on the USPTO site with "spec/vt100 and spec/buy and spec/item and spec/list" returns six patents including:
MinitelThe Minitel uses a public X25 network. There is a better page on French Wikipedia.
The end-user is provided a Minitel device with a asynchronous modem. The modem dials a phone number and connects through the phone to a Packet Assembler/Disassembler that can be hosted by the TELCO. The PAD translates asynchronous flow sent by the modem into X25 packets and sends these packets through the packet-switched network to the server DCE. A typical use was the following:
A search on USPTO with "(spec/minitel or spec/prestel or spec/napls or spec/bildschirmtext or spec/videotex) and spec/buy and spec/item and spec/list" returns ten patents, including:
BBSBBSs addressed the same technical (file transfer) and social (e-mail, online chat and conferencing) needs as Internet today. However BBSs had far less users and were marginally a market place. To be more precise BBSs were used to sell but very little was automated. The reasons for that were:
There were three kinds of interface:
There were numerous BBS programs. At least one of them survived, Citadel. There were many forks in Citadel code. There is a page listing the variants. Beside BBS there were:
"Initially, Prodigy had hoped that its service would be much like today's Internet portals, offering news, weather, sports, shopping for groceries or general merchandise, banking, brokerage services, and airline reservations." "Prodigy retains the distinction of having launched ESPN's website and growing such firms as PC Flowers into some of the online world's earliest success stories."Airline reservation and flowers are businesses for which 1-click makes sense. Users were using client programs such as Kermit, the XModem, YModem, ZModem file transfers, the front end softwares of CompuServe (TAPCIS, ATO, CISNAV and Navigator) and Prodigy, and programs like QModem and Crosstalk.Summary
|
Patents Presentation Search Issues Strategies Business Methods Patentability Analysis MercExchange eBay Trial Reexamination Business view Granted patents Examination USPTO EPO PanIP Eolas 1-click family 1-click analysis 1-click prior art Trademark Copyright
Contact:support@pagebox.net
©2001-2005 Alexis Grandemange
Last modified